
Posted on 2022-10-17 by Nathan Jarvie in Industry
Part 3 of the Sysadmin-to-Pentester series is all about how to make your CV stand out from the crowd. Junior roles are rare with many many applications. Additionally, hacking skills don’t translate well to text. So how do we show we have more skill and drive to be a penetration tester than the other candidates, on paper? Well…
Advice for the uninitiated
There are thousands of blog posts and videos on the internet describing how to become a pentester. While they are all valid and helpful, none of them will provide someone with a bulletproof way to get into the industry, because there isn’t one.
Since getting into the industry myself, I have a better understanding now of how to stand out in the hiring process and I wish to share that with you.
Here are a few things I wish I did before I started applying for jobs.
We need a tailor over here!
I cannot stress this enough: You must tailor your CV to the role you want.
While it is not unheard of to jump straight from university to penetration testing, it is very rare and a leap reserved for those who have been networking and passionate for years. For the rest of us we need to take a different route and the skills you learn on the way can make the difference in job applications.
Highlight your personal skills and your passions. The person reading your CV should get an idea of who you are as a person from your CV. Listing out all your skills in dot point form and not speaking about yourself and what you are passionate about is a quick way to get your CV filed away in the bin.
Alexei did a wonderful workshop recently on this very topic. I highly recommend you spend the time watching it as his experience is better than any advice I could ever give.
Capture the Flag - Report writing tutorials in disguise
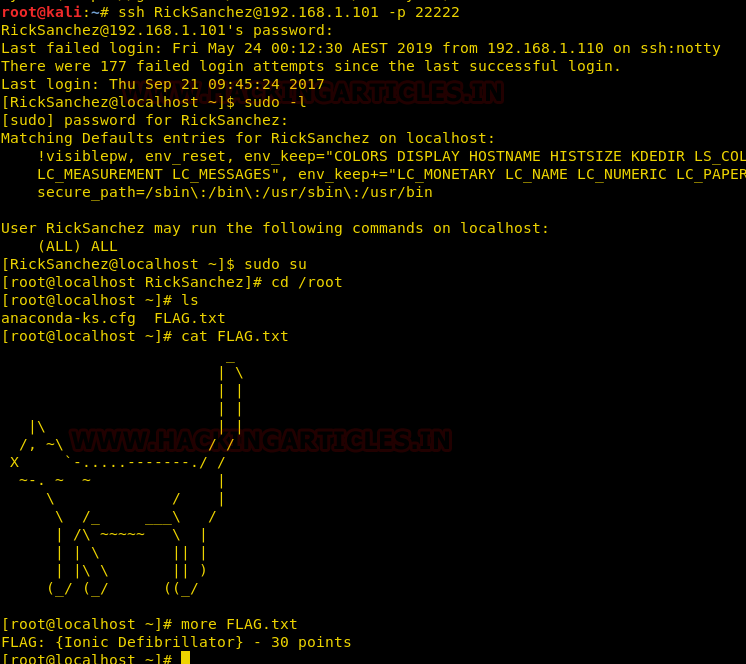
It is common for many “How to become a pentester in 30 days” blogs to say do Capture the Flag (CTF) write-ups and put a link on your CV. You should absolutely do that, no question about that. But… What if you can do one better. What if you can give your potential employer a real taste of your skills in a way that NO ONE ELSE is doing?
CTF’s, though often somewhat unrealistic, provide an excellent opportunity to sharpen your technical skills and optionally, your report writing skills.
While doing a CTF, take screenshots of everything of value, then turn those screenshots into a report outlining the attack walkthrough. Put it on your blog, good. Now you have done what everyone else is doing. Let’s go one better.
Spend some time researching the vulnerability that was exploited, what is it at a high level, and how to remediate it. Write a vulnerability write up explaining what you have discovered and put it in the context of the CTF. Imagine that CTF is part of a fictional organisation, and you found it on their internal network. How impactful would exploitation of that vulnerability be to your client?
Summarise the whole report into an executive summary using non-technical language. Put it all together in a pentest report. Now put that on your blog instead.
Providing a link to your blog with a few full pentest reports to potential employers can give them an idea of your technical skills, your technical writing and your executive writing abilities. This demonstrates to a recruiter or hiring manager that you understand that pushing buttons is only part of the gig and why they worked, and what that means to a client is equally or more important. This is a big advantage for junior pentesters and could be the deciding difference between you and other candidates.
You do not need to do this for every CTF you do, but 3-5 examples could make the difference in getting an interview. There are hundreds of templates online for pentest reports so choose one that works for you.
Here’s a shameless plug, but Volkis make a fantastic reporting tool that you can use called ReportRanger which can be found here:
Training platforms - So what…?
Advertising on your LinkedIn and your CV that you develop and practice skills on training platforms is great; it shows an interest in self-learning. This is especially important if you don’t have any experience in the industry.
HackTheBox, TryHackMe, PentesterLab, Offensive Security’s Proving Grounds, there are heaps of different ways to learn and they all have a pile of different challenges. Not every challenge type is interesting to everyone so highlight what you like doing. This helps recruiters to understand what type of hacker you are and whether you will fit in with their requirements.
Don’t put “Top 5% on TryHackMe” or “Pro Hacker rank on HTB” in your LinkedIn headline and expect that recruiters will come flocking to you. Rather, put your platform of choice in your bio somewhere with some context, like completed learning paths, CTFs or Networks and some information about what challenges you enjoy. If you can, link those challenges with the pentest reports you have posted on your blog.
Web Applications - Learn to love them
On the topic of training platforms, take particular note of challenges or learning paths that involve Web Applications. These come up a lot in penetration tests and getting comfortable in testing them opens a lot of doors. Many big name companies, like financial firms, have their own small army of Web Application and Mobile Application penetration testers. They are always looking for new talent.
I was lucky enough to score a meeting with two pentesters from a well known Australian bank while I was applying for roles. They took the time to explain to me that banks and other large firms have a requirement that their projects are pentested before they are released to the client. They always have a back log and need pentesters. While other areas of pentesting are useful, they want people with a real passion and drive for web applications.
Take the opportunities to learn as much about web application security as you can. There are courses and books available on Web Application hacking. Online training platforms like Portswigger’s Web Security Academy and PentesterLab, or offline versions like OWASP JuiceShop, Damn Vulnerable Web App (DVWA), or bWAPP are fantastic resources that are worth the time investment early on.
Bug (beg?) Bounties
Many people wanting to move into penetration testing will see Bug Bounties as a way to get their name out in the industry and maybe make some money on the side. I personally do not have any experience with bug bounties, so I asked Alexei who gave me this advice to share with you all:
I think choosing a “kudos” bug bounty target and using them for practice is a great way to learn. Not many testers are attacking them because there’s no cash reward, so there’s a good chance there are still vulnerabilities to find. This also counts as real-world experience and looks great on a resumé.
Network Labs - I can’t believe it’s not a pentest!
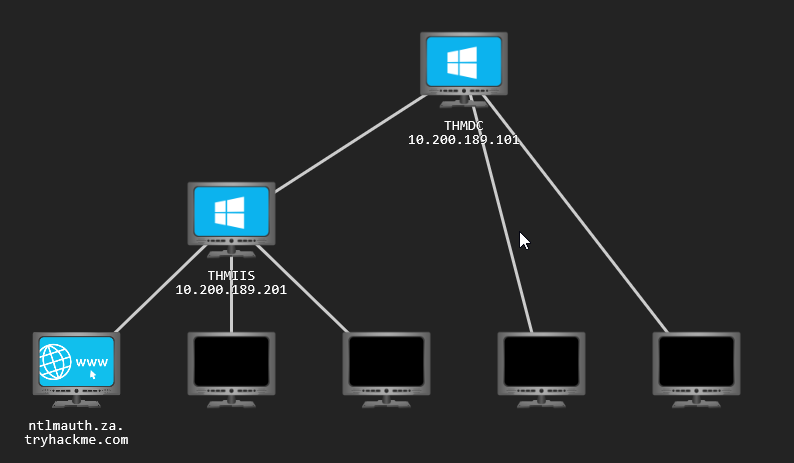
Some of the training platforms have more advanced labs involving multiple systems in a network. These are fantastic training grounds for learning techniques that are otherwise difficult to understand, such as looting and pivoting. These labs are deliberately vulnerable and have a designed path you can take through the lab to get to the final flag but the techniques and notes you gain through this experience is invaluable.
For a more realistic approach you can roll your own environment. Some of the courses will help you to build your own home lab environment. I highly recommend that you do this. Build out a functioning (virtual) Active Directory environment, from scratch. This will help you to understand how all the pieces of a network fit together and provide a better overall understanding of the power of Active Directory.
Keep it up to date and take snapshots (so you don’t have to build it all again when you break it). You can use it to test a variety of exploits or attempt to bypass security settings, then fix it and see if it still works.
Understanding how networks and Active Directory work will help to better understand the impact of a vulnerability, and help you to write better reports and remediation advice.
Home labs are an excellent topic in interviews.
(Social) Networking - Talking to people is good!
I had an unfortunate handicap here as there were no in-person conferences held while I was completing my studies due to the pandemic. As such I missed a very important and somewhat overlooked aspect of InfoSec: The community.
This industry is heavily reputation driven. This appears to be true, not just in Australia but all over the world. As such, many opportunities for InfoSec roles do not come from Seek or Indeed, but rather from networking at conferences, or in Slack and Discord channels.
Get involved in:
- Join InfoSec based Discord servers (there are hundreds of them)
- Join a CTF team
- Get on Twitter and follow companies and content creators
- Comment on YouTube videos
- Get involved in Twitch streams
- Connect with people on LinkedIn and comment on posts you like
- Get to conferences and meet people in person
Get involved in the InfoSec community as much as you can. Go out and meet people, join a virtual community, provide assistance to those trying to learn where you can, and most importantly, don’t be toxic! Be seen as someone helpful and knowledgeable in the community and opportunities will present themselves with a lower candidate pool.
It is also valuable to include your community involvement in your CV. That could be coding projects you have contributed to, talks and conferences you have enjoyed or presented at, or events you have participated in. These show a deeper passion about the role than simply learning the skills.
Also, one last tip. Try using TweetDeck to manage your Twitter feeds into something more sensible.
On the next episode…
In the next post in my small novella, I walk through some of the certifications and courses I have completed that have proven been valuable. A zero-to-hero of pentesting, if you will.
Next: Part Four - Tickets please
Previous: Part Two - Great expectations
About the author
Nathan is certification addict, he can’t stop and it’s becoming a problem. We can’t talk to him about it directly but consider this a call for help.
If you need help with your security,
get in touch with Volkis.
Follow us on Twitter and
LinkedIn