Posted on 2022-10-31 by Nathan Jarvie in Industry
Part 5 of the Sysadmin-to-Pentester series is a comparison between two entry level penetration testing certifications. Offensive Security’s Certified Professional (OSCP) and TCM Security’s Practical Network Penetration Tester (PNPT). While both have their merits, they focus on different elements and provide different experiences. Deciding which to go for can be a challenge.
Choose your fighter
Referring back to the previous post for a moment, when deciding which “foundational pentesting certification” course to take, there are many factors to consider. There are a number of options available on the market that all, in essence, teach the same things. The difference is how they go about it and the topics that they focus on.
Some focus heavily on giving you the theory behind every attack but not much in the way of how to actually do it. Others will focus on the practical and only give you enough information for you to understand why. Others still are more focused on the adjacent topics like technical writing. So which one is for you? As I said before, it depends.
There are over 430 IT security related certifications with 74 of those being directly related to penetration testing or exploitation. A full list is provided by Paul Jerimy and can be found here:
I have taken four (?!) different “foundational level” exams for penetration testing. Perhaps one day, just for fun, I will work through more of them for comparison sake; but for now I have completed:
- CompTIA Pentest+
- EC-Council Certified Ethical Hacker - CEH
- TCM Security Practical Network Penetration Tester - PNPT
- Offensive Security Certified Professional - OSCP
Just comparing the ones I have done, what is most interesting is how much “foundation-level” exams vary in content and difficulty. The infographic provided in the link above shows that better than I can.
From experience, I can tell you that the first two (Pentest+ and CEH) are only valuable if you work in particular countries or are looking for specific jobs with government agencies, or perhaps as a stepping stone between your current role and pentesting. They are both very heavily theory based and have multiple-choice style exams, though a practical component is available for CEH to upgrade your certification to “Master”, but it is very short. While I learned a lot from their courses, I found other certifications are a better investment.
As such, I am going to focus on the last two: PNPT and OSCP.
Please bear in mind that attempting the exam places the certificate holder under an NDA, so the exact content of the exams cannot be discussed publicly; thus the content of this article is intentionally vague.
The Weigh-in
Both of these courses follow a similar format:
- Work through the course materials
- Complete the exercises
- Do some additional practice
- Sit a practical exam
- Submit a report
Seems pretty straightforward, right? So which one is better? Well, I believe they are for different things and which one you take (or which order you take them in if you wish to do both) depends on what you are trying to achieve.
PNPT is focused on teaching the student how to be a penetration tester. That is to say, how to do the job from start to finish. Where OSCP teaches the student how to hack machines, with the idea that you will learn how to do the job once you are in it. Both schools of thought are valid, and they both have their place in the industry. So before we jump straight into a course, let’s get a better look at both.
PNPT
TCM Academy and the PNPT certification were released in April 2021. Being a relatively new certification it is not yet as well known as OSCP, which is a certification that is recognised even by those who are not in the infosec community. This is changing slowly and the certification is gaining a lot more interest now.
As of the time of writing, PNPT has been requested in over 50 job postings in over 10 countries (including the likes of big players such as Tenable and Paramount). US Government agencies have purchased the training and certifications for their staff. And while there is a long way to go to match OSCP in recognition, the foundations for success are there.
So here are the stats:
- There are over 950 certified PNPTs (since October 2023)
- There is a 35.44% pass rate on the first attempt (stated by TCM staff on their public Discord server in March 2022)
- Training package includes 5 courses (approx 55 hours of video content) + exam attempt + 1 free retake
- Cost is US$399 with training.
- 20% discount is available for students, first-responders, military and veterans
- Occasional sales advertised on Twitter and LinkedIn
OSCP
Offensive Security’s OSCP certification is one of the most coveted penetration testing certifications on the market. This is primarily due to the recognition by IT and non-IT recruitment and it’s reputation as being exceptionally difficult to pass. The certification is a common addition to job postings and is considered by the community to be a gate-keeping certification. That is to say that those who do not understand what penetration testers do (HR officers for example), will use it to filter out candidates before interviewing them.
It was release in 2006, and went through it’s most recent updates in January 2022, which changed the format of the exam to (almost) require the compromise of an Active Directory environment. Further updates were added to the training platform in March 2022 to streamline delivery of content and improve the lab exercises.
Offensive Security do not release statistics. A paraphrasing their official stance as: “We do not wish to needlessly demoralize students with this information”. Therefore, we have to rely on some napkin-maths and hearsay for our stats.
- Less than 40% of students pass on the first attempt, with some estimates being less than 30%
- Cost is either subscription based or US$1599 (includes one exam attempt and 90 days lab time)
- Lab extensions and exam retakes are purchased separately
The Main event
Both courses have accompanying training materials that should (in theory) lead you to a successful exam attempt. However, the method of training and priority in both courses is completely different and as such are likely to provide different perspectives on pentesting.
PNPT
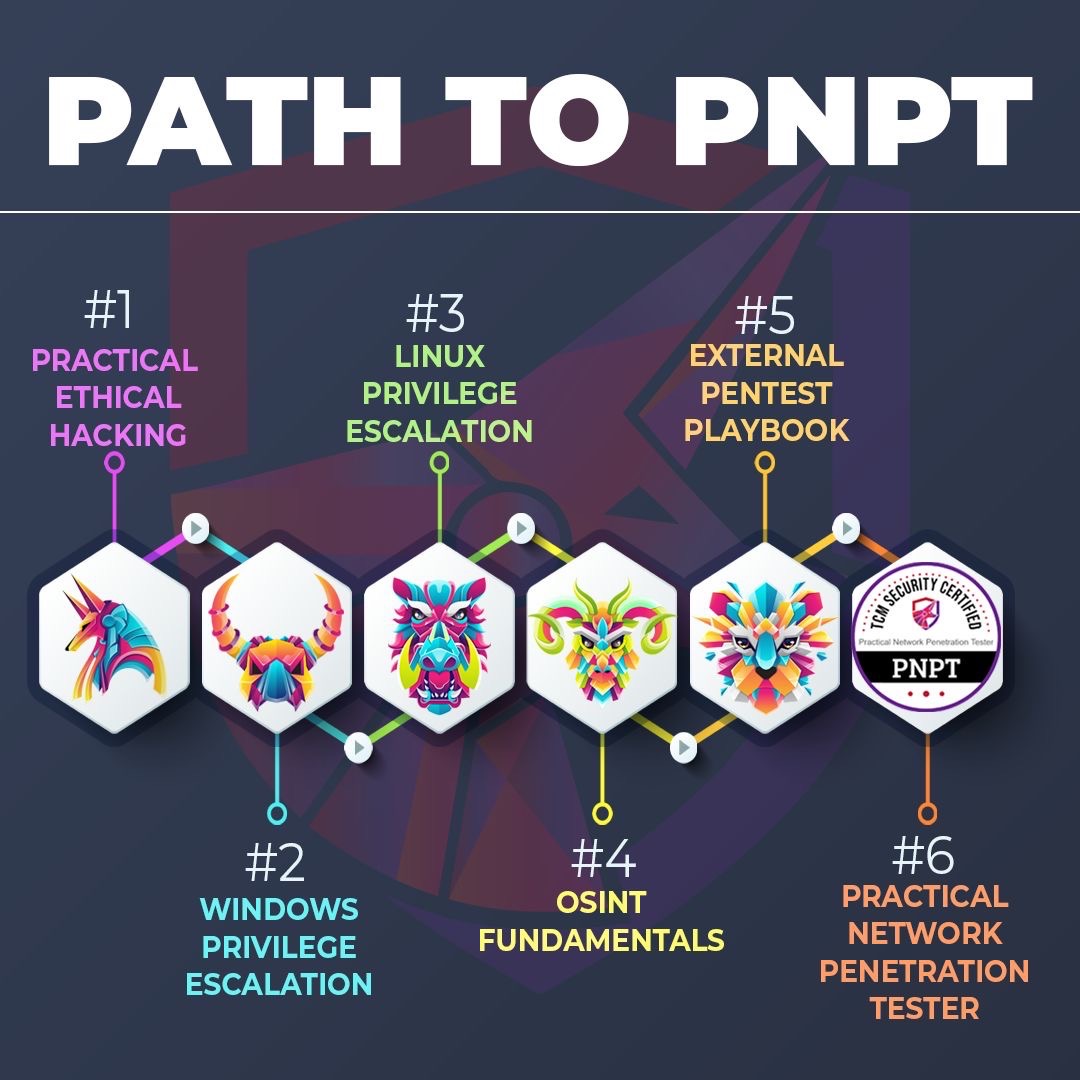
The PNPT training materials consists of 5 separate modules:
- Practical Ethical Hacker (PEH)
- Open-Source Intelligence Fundamentals (OSINT)
- External Pentest Playbook (EPP)
- Windows Privilege Escalation (WPE)
- Linux Privilege Escalation (LPE)
The bulk of the training is in PEH, which walks through all the aspects of being a pentester and provides some interesting hacking-adjacent commentary. The remaining modules build on this with more advanced concepts and additional practice. Overall the course covers a variety of topics and provides enough information that you understand the subject, how to do it and where to find more information if you need it. While the topics covered between the foundational courses are similar, there are a few clear priority differences. TCM Security have additional focus placed on:
- Active Directory
- Web applications
- Wireless
- Open-Source Intelligence
Additionally non-technical topics that are fundamental to a pentester have been given more priority throughout the instructional content than other courses.
- Note taking and organising
- Report writing
- Pentest structure - Including scoping, testing etiquette and clean-up
- Client communication
Throughout the course you are directed and encouraged to play around on different learning platforms, such as TryHackMe and OWASP Juice Shop. You are also encouraged to build your own Active Directory environment in a home lab, in which you can test a variety of configurations and their remediation. This approach allows for a more in-depth understanding of how a client’s network may be configured and allows you to play with different settings and configurations. The downside here is that you do need a reasonably powerful computer to run 3-4 virtual machines at the same time, which can be a limitation for people.
All content is provided in the form of streamed videos through the Teachable platform, which has it’s own limitations. Though it is worth noting that a large portion of the course is available for free on YouTube, which can give you a good feel for how it flows before you pay for it.
For additional practice before the exam I recommend the TryHackMe networks. Though you have to pay for them separately they are absolutely worth the investment.
Optionally you can also work through TheMayor’s Movement Pivoting and Persistence (MPP) course, which has some super valuable tricks in it.
OSCP

Offensive Security have a few different methods for delivering their content, and while the content is the same across all mediums, the delivery method is different.
Everyone who signed up pre-April 2022 (including myself) received a PDF containing all the course material and videos that covered that same content. Students who signed up after April-2022 can access their content in the “Training Library”. By all reports this method is much better than the PDF/videos but I have not experienced it yet.
The content of the materials is typical of any foundational-level pentesting course. It walks through the basics of the linux commandline and then moves on to the attacks and how they work. There is a small section on report writing, web applications and Open-Source Intelligence but these areas do not go into a huge amount of depth. While I had already completed several entry-level courses by this point, I did learn a few tips and tricks that proved to be handy later. So don’t write it off based on that alone.
Additionally, a set of exercises is provided within the materials that can be completed for 10 bonus points on the exam. You need to provide two additional reports during the submission of your exam report:
- The exercise report - A document containing the workings and answers to the exercises in the course. I understand that this has been made easier now with the training Library
- The lab report - Walkthroughs and documentation for 10 machines in the PWK lab environment including at least 1 AD set.
The meat of the course comes in the form of the Student Lab environment. Multiple networks and interconnected vulnerable machines that can be exploited to practice your newly developed skills. OffSec’s mantra of “Try Harder” comes into play here as there are no walkthroughs for this content. You must work through them piece by piece until you find you way through the maze. Hints are available in the student forums, but they are provided by other students so they are not always helpful.
I suggest attempting a box for a set period of time (set a timer) and if you do not progress, check the forums if the box has any dependencies. You may find you are missing information and exploitation is not possible without it.
There are different opinions on how much of the student lab you need to complete to feel “ready” for the OSCP exam. Personally I found I lost interest in the environment when the remaining non-domain boxes were overly dependant on exploitation of another. The Active Directory environments were an absolute must-do and they were great practice for both the exam and the real world.
The problem with the labs is that they are shared with other students. On more than one occasion I breezed through a machine many considered hard before realising that it had already been compromised by another student, and I was piggybacking off their work. So now i had to make a choice: Ignore it and move on, having learned nothing from a difficult machine, or reset the machine and do it again, but you already know part of the exploitation path. Other times I would have my shell or my pivot dropped by another student resetting a machine to avoid that exact scenario.
The experience was valuable but so frustrating that I went looking for training material elsewhere; namely Offensive Security Proving Grounds, which I mentioned in the previous article.
Adjudication
So we’re through all the training materials and feeling reasonably confident. Excellent. Time for the exam itself.
Both the exams for OSCP and PNPT follow a similar format in that they are practical and require you to actually compromise systems, and also require a clear report with which a technically competent reader could follow to achieve the same results. All of which must be completed within the allotted time frame.
The differences lie in the realism, the testing conditions and the requirements for success. I put together this quick comparison of the two exams here to make it easier to see the difference, but read on for more details.

PNPT
The PNPT exam broken into 3 parts:
- Practical exploitation
- Report
- Debrief
You are provided a document at the beginning of your exam and your VPN package for the environment. The document contains clear Rules of Engagement (ROE) and the scope of the exam. You should read this document carefully at least twice and make sure you understand it all because going out of scope will lead to a fail.
This exam has no points structure, it is simply pass or fail based on whether you meet the criteria: Compromise the Domain Controller. You have 5 full days to complete the objective.
There are no tool restrictions in the environment. You can use whatever you feel comfortable with. That includes Metasploit, PowerShell Empire, Burp Suite Pro, SQLmap, whatever you like.
Once complete, you have to write a professional pentest report with vulnerability write-ups and remediation advice. You also need to include an executive summary for non-technical readers and attack walkthrough for technically competent people to follow. It should demonstrate that the work completed and the impact of exploitation in a way that is understood by the client. The report must be submitted within 2 days of the end of your practical exam.
Lastly you have to complete a 15-minute debrief with a senior penetration tester (who is pretending to be the client). Honestly this part is not as bad as it sounds. You have to prove your identity then explain your report. I did mine using the report itself and summarising each section. I did also spend a long time on a PowerPoint presentation I didn’t use, so that was a waste of time. The point of the debrief is two fold:
- Prove you actually did the work and understand the concepts in the exam by having to explain it and answer any questions.
- You would have to do this on a real pentest so it’s good experience.
All-in-all the exam was as close to a real pentest as you can get. All the skills and techniques you need to pass the exam are provided in the training; honestly they are.
OSCP
The exam for OSCP certification is a beast in itself.
It is a points-based fully proctored exam, so the objective is to obtain 70 points (or more) within the time limit from an Active Directory environment and 3 stand-alone machines. You are allocated 23 hours 45 minutes to complete the objective.
The AD environment is worth 40 points and requires the compromise of the Domain Controller. No partial points are awarded here. The remaining three machines have two flags worth 10 points each, for a total of 60 possible points. That means if you complete your lab exercises and lab report, it is possible to achieve a passing grade without the compromise of the AD set.
The environment is “randomly generated” in that there are a pool of possible AD networks and machines that can appear on the exam and you will get a different combination than someone else. The issue with that is that some machines are harder than others and it is possible that you will get a full set of hard machines where someone else gets a set of easy machines. There have been stories of people sitting and failing their first attempt, then breezing through the second purely based on the machines you get on the day. I personally had one machine that I am convinced was broken and had no possible way to be exploited, but maybe I just couldn’t work it out.
Please note that unlike PNPT this exam is proctored, so you must have your camera on at all times while using the lab environment. This is a major sticking point for a lot of people. Additionally, there are strict restrictions on tools used in the exam. Don’t bother emailing Offensive Security about it though because they will not respond. Here is what I have deduced:
Definitely Restricted
- Metasploit/Meterpreter - Can be used ONCE and if it fails bad luck. BUT you can use
multi/handlerwhenever you like so long as you aren’t using meterpreter payloads. (Though to be on the safe side, just usenetcat) - Powershell Empire - technically allowed but many modules are not, and you have to guess what is and isn’t. Better to avoid.
- SQLMap - Cannot. Do not.
- Anything with AutoPwn utilities. If you just need to point and shoot, it’s out.
- All purchased tools (Burp Suite Pro, Nessus, Cobalt Strike, etc)
Allowed tools that people often ask about
- Impacket suite
- CrackMapExec
- AutoRecon
- LinPeas/Enum4linux/any enumeration script - If it doesn’t actually exploit anything, it’s good
The short and nasty of it is that if you don’t know if it’s restricted, don’t use it. Use scripts and exploits from exploitdb, GitHub, anywhere you like, but tools are different and disqualify you if you aren’t careful.
You also have to submit a report on your findings within 24 hours of completion of the practical. This is less detailed than the PNPT version and just consists of a short exec summary, an attack walkthrough and a description of the vulnerabilities exploited. Full vulnerability writeups are not required.
What makes this exam difficult is that you are proctored during your allotted lab time. Someone is watching you work to ensure you don’t cheat. When that is combined with the time pressure of a 24-hour exam, it can make for a very stressful and unpleasant experience.
Tallying the scores
While I believe my opinion can easily be inferred from the above, there are some more factors to take into consideration.
Each course had it’s own merits and both taught me valuable skills. There were tips and tricks that I learned that I will use every day of my career from each. However, choosing which course is appropriate for you may be different. Here are some pros and cons of each option:
PNPT
| Pros | Cons |
|---|---|
| Much cheaper than the competition | Not as well known in the industry yet |
| Lifetime access to courses and content updates | Small community, primarily in Discord |
| Large focus on OSINT, Web applications and Report writing | Courses only available through video and can’t be viewed offline |
| Encourages students to build (and exploit) their own labs | Platform is clunky to use (provided through Teachable) |
| Introduces students to other platforms (TryHackMe, HTB, etc) | No hosted labs |
| Large amount of the course is available for free on YouTube | Can be limiting for those without moderate to powerful systems as practical examples may require a hypervisor and sufficient resources. |
| Customer service is excellent | |
| Helpful community |
OSCP
| Pros | Cons |
|---|---|
| Industry recognized | Expensive |
| Certification is recognized by adjacent industries | Training environment is shared |
| Online Training labs included | Labs have dependencies |
| Large community (Discord, Reddit, OffSec forums) | Customer service is canned (and useless) |
| Student Admins are helpful | Have to go far outside the materials provided to learn enough to pass |
The Winner is…
PNPT
I honestly believe that the course and accompanying certification will produce more capable penetration testers over the long term. There is more focus on what the job actually entails; including technical and non-technical skills. It includes training on skills not covered sufficiently or at all in the PWK syllabus:
- Report writing
- Keeping in scope (and the consequences if you don’t)
- Methodologies
- Web applications
- Wireless
The course was easy to follow and the community are helpful if you do have issues. They legitimately want to see everyone succeed and it shows. TCM Security are transparent in what they want to achieve, they suggest additional external resources for learning and have built a supportive community that wants to give back as much as it receives. In essence, all the same things that Volkis encourages and puts into the community.
Whereas I found that the PEN-200 (PWK/OSCP) materials did not give any impression at all of what being a pentester actually means. The PWK resources were very clinical and technical, with the idea that if you “try harder” you will be successful. While that is true to an extent, I don’t believe it is the best mentality while you are learning. It feels like the InfoSec version of “git gud scrub”, which I hate. You don’t know what you don’t know and can’t be expected to “just work it out” when you have paid for training specifically because you do not know it.
It will take a while before PNPT holds a status like that of OSCP in the industry, but if more people achieve it and talk about it, and are proud of it, I think it won’t be long before it’s up there with best.

Conclusion
Thank you for taking the time to read these posts; I know they were long. I hope that whatever stage you are at in your journey, you got something out of them that may help you. Becoming a penetration tester is a not easy, and made more difficult by the lack of entry-level positions available world-wide, but I encourage you to not give up hope.
For those just beginning your journey, I hope my experiences help to streamline your own success.
For those who, like me, are changing careers. You can do it and it is worth it. My mental health has improved dramatically by changing from a job I was good at to a job I enjoy. I cannot recommend it enough. Start now and you will be surprised how quickly it comes.
For those who are a little younger, coming out of high school or university, work hard and keep your head up. Get out to conferences and talk to people. Members of the industry want to help and guide you, so please reach out and make friends. It’s your best chance to getting into infosec.
If you see us at cons, please come and talk to me or any of the Volkis team! We will probably have stickers or something to share with you. Or reach out on social media; we are always happy to connect and chat and offer advice where we can.
You can find me on LinkedIn and Twitter. Or connect with Volkis also on LinkedIn and Twitter.
Thank you, good luck and happy hacking.
- Nathan Jarvie (Kinryu)
Previous: Part Four - Tickets please
About the author
Nathan is certification addict, he can’t stop and it’s becoming a problem. We can’t talk to him about it directly but consider this a call for help.
If you need help with your security,
get in touch with Volkis.
Follow us on Twitter and
LinkedIn